|
#4
16th August 2014, 02:11 PM
| |||
| |||
| Re: Previous year question papers of UGC NET of Computer Science and Applications
As you want to get the previous year question papers of UGC NET of Computer Science and Applications so here it is for you: Some content of the file has been given here: 1. The postfix expression AB + CD – * can be evaluated using a (A) stack (B) tree (C) queue (D) linked list 2. The post order traversal of a binary tree is DEBFCA. Find out the preorder traversal. (A) ABFCDE (B) ADBFEC (C) ABDECF (D) None of the above 3. The branch logic that provides making capabilities in the control unit is known as (A) Controlled transfer (B) Conditional transfer (C) Unconditional transfer (D) None of the above 4. The number of colours required to properly colour the vertices of every planer graph is (A) 2 (B) 3 (C) 4 (D) 5 5. Networks that use different technologies can be connected by using (A) Packets (B) Switches (C) Bridges (D) Routers 6. Both hosts and routers are TCP/IP protocol software. However, routers do not use protocol from all layers. The layer for which protocol software is not needed by a router is (A) Layer – 5 (Application) (B) Layer – 1 (Physical) (C) Layer – 3 (Internet) (D) Layer – 2 (Network Interface) 7. In multiuser database if two users wish to update the same record at the same time, they are prevented from doing so by (A) Jamming (B) Password (C) Documentation (D) Record lock 8. A binary search tree is a binary tree : (A) All items in the left subtree are less than root (B) All items in the right subtree are greater than or equal to the root (C) Each subtree is itself a binary search tree (D) All of the above 9. What deletes the entire file except the file structure ? (A) ERASE (B) DELETE (C) ZAP (D) PACK 10. Which command is the fastest among the following ? (A) COPY TO <NEW FILE> (B) COPY STRUCTURE TO <NEW FILE> (C) COPY FILE <FILE 1> <FILE 2> (D) COPY TO MFILE-DAT DELIMITED For more detailed information I am uploading PDF files which are free to download: Previous year question papers of UGC NET of Computer Science and Applications     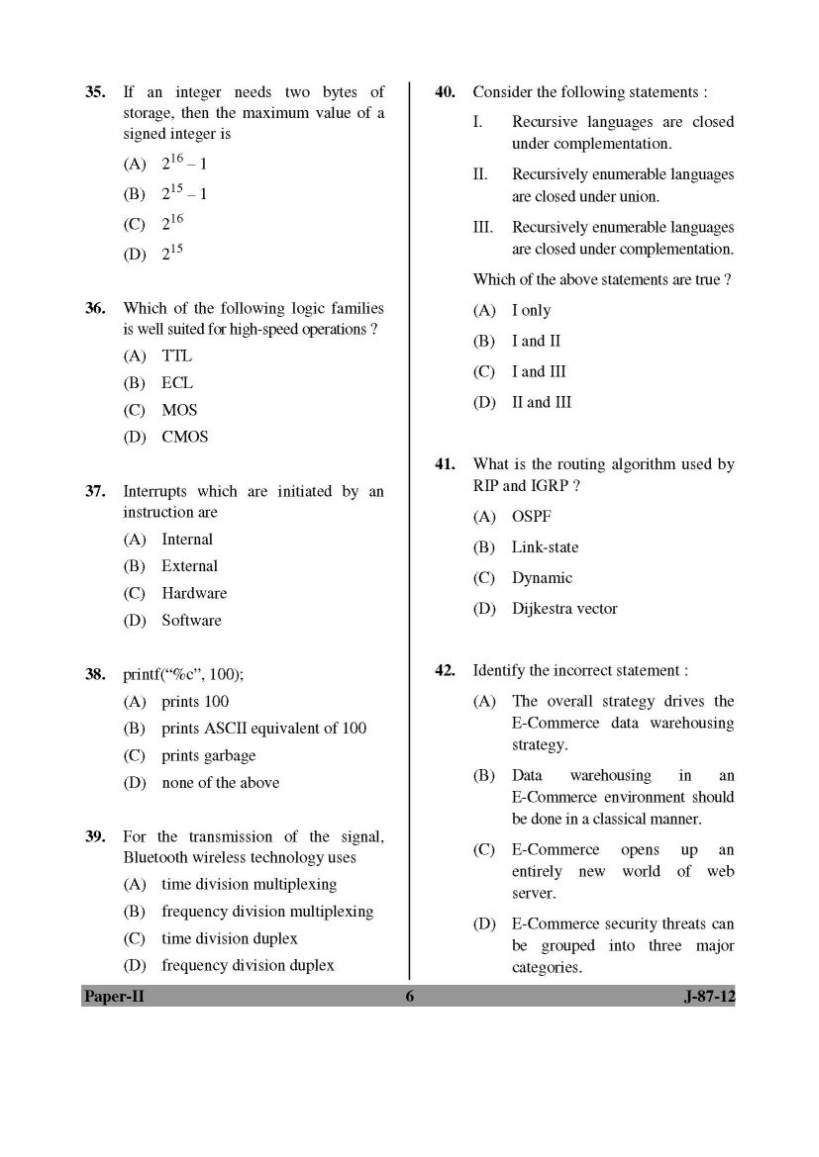  |