|
#2
21st July 2015, 05:28 PM
| |||
| |||
| Re: IIT Kanpur last GATE Paper
You are looking for IIT Kanpur GATE Computer Science / Information Technology (CS/IT) question paper here I am giving: A binary operation ⊕ on a set of integers is defined as 2 2 y x y x + = Å . Which one of the following statements is TRUE about ⊕? (A) Commutative but not associative (B) Both commutative and associative (C) Associative but not commutative (D) Neither commutative nor associative Which one of the following is the tightest upper bound that represents the number of swaps required to sort n numbers using selection sort? (A) O(log n) (B) O(n) (C) O(n log n) (D) O(n2) Which one of the following is the tightest upper bound that represents the time complexity of inserting an object into a binary search tree of n nodes? (A) O(1) (B) O(log n) (C) O(n) (D) O(n log n) A scheduling algorithm assigns priority proportional to the waiting time of a process. Every process starts with priority zero (the lowest priority). The scheduler re-evaluates the process priorities every T time units and decides the next process to schedule. Which one of the following is TRUE if the processes have no I/O operations and all arrive at time zero? (A) This algorithm is equivalent to the first-come-first-serve algorithm. (B) This algorithm is equivalent to the round-robin algorithm. (C) This algorithm is equivalent to the shortest-job-first algorithm. (D) This algorithm is equivalent to the shortest-remaining-time-first algorithm. The transport layer protocols used for real time multimedia, file transfer, DNS and email, respectively are (A) TCP, UDP, UDP and TCP (B) UDP, TCP, TCP and UDP (C) UDP, TCP, UDP and TCP (D) TCP, UDP, TCP and UDP Using public key cryptography, X adds a digital signature σ to message M, encrypts <M, σ>, and sends it to Y, where it is decrypted. Which one of the following sequences of keys is used for the operations? (A) Encryption: X’s private key followed by Y’s private key; Decryption: X’s public key followed by Y’s public key (B) Encryption: X’s private key followed by Y’s public key; Decryption: X’s public key followed by Y’s private key (C) Encryption: X’s public key followed by Y’s private key; Decryption: Y’s public key followed by X’s private key (D) Encryption: X’s private key followed by Y’s public key; Decryption: Y’s private key followed by X’s public key An index is clustered, if (A) it is on a set of fields that form a candidate key. (B) it is on a set of fields that include the primary key. (C) the data records of the file are organized in the same order as the data entries of the index. (D) the data records of the file are organized not in the same order as the data entries of the index. IITK GATE CSIT exam paper 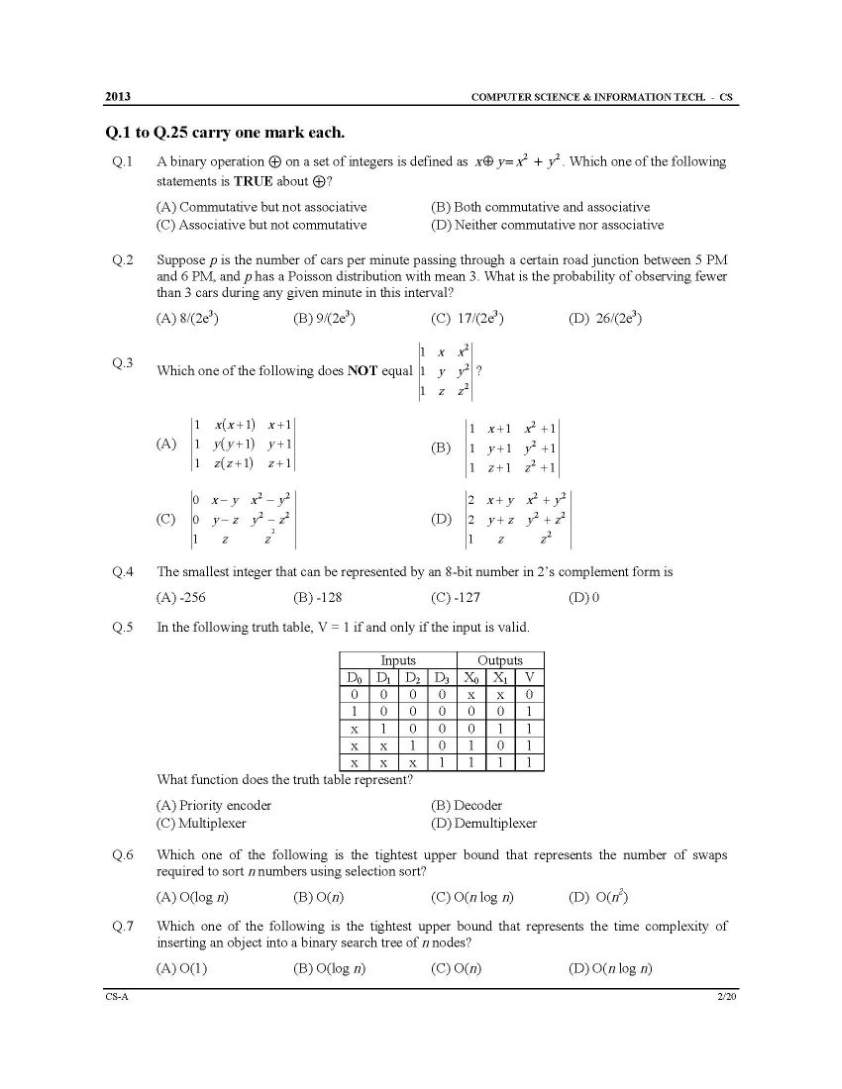  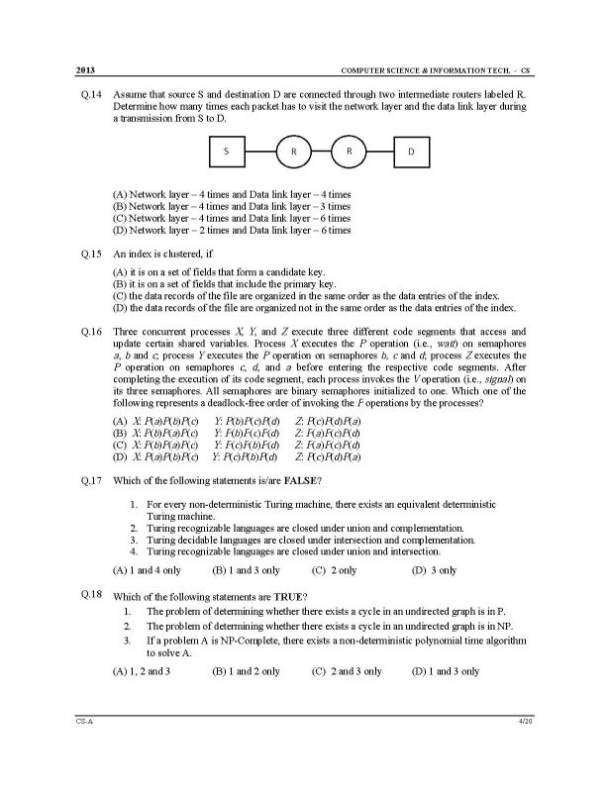   For detailed question paper, here is attachment: |